This work has been published in IEEE ICIP’15 conference.
Principle
In the Selective Encryption (SE) approach, it is of prime importance to distinguish the two different security aspects that have to be addressed. On the one hand, the content security mainly depends on the available ES : the more codewords you are able to encrypt, the more the reconstructed frames will be distorted. On the other hand, the encryption security is directly related to the robustness of the encryption algorithm used, i.e. the way pseudo-random bits are generated (PRBG in figure below).
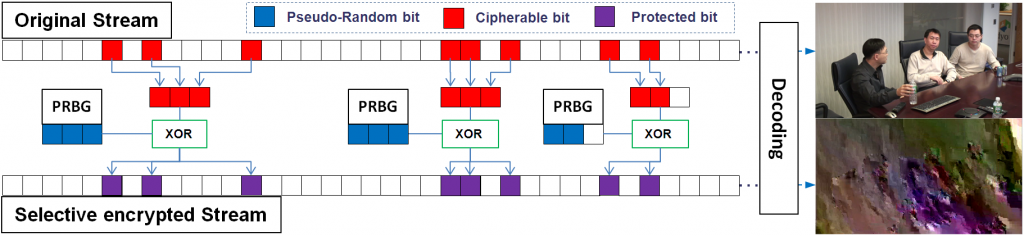
Selective Encryption performs bit-wise analysis of the stream. Cipherable data is XORed with a ciphertext (or a pseudo-random sequence). The ciphertext is here generated by a Pseudo-Random Bit Generator (PRBG).
Numerous encryption algorithms coexist in the literature, but we will focus our study here on algorithms that have been used within SE approaches. In [1], different solutions are proposed (the Rivest’s cypher RC5, the Data Encryption Standard DES, the Advanced Encryption Standard (AES), etc.), while they finally select the AES in Electronic Code Book (ECB) mode for speed purposes. The AES is an algorithm developed by Daemen and Rijmen in 2001 and selected by the NIST (National Institute of Standards and Technology) [2]. Its robustness and ease of use makes it one of the best candidates for monitoring SE, and has been widely used in this context: Shahid et. al., in their works on H.264 ([3], [4]) and HEVC [5], as well as Wallandael et. al. ([6], [7]) are typical examples of this trend.
Nevertheless, in real-time wireless communications (e.g., RTP-supported), the encryption scheme has not only to be robust against cryptographic attacks, but also against errors and erasures: the preservation of the synchronization between encryption and decryption becomes critical too. In such a context, applying encryption algorithms with feedback (where computing the ciphertext requires information of the previous block cipher) like the AES-OFB (Output Feedback) or AES-CFB (Cipher Feedback) as in [5] is highly unadapted. In case of a lost RTP packet, all the subsequent packets are not decipherable. This specific issue has been addressed in a few papers: in [8], real-time synchronization is performed with a chaotic cryptosystem. Such an approach has some important drawbacks: the computing power needed is non-negligible, additional data (the drive signal) has to be sent, and latency is induced before master and slave systems are synchronized. In [9], a method based on the Diffie-Hellman key exchange is proposed, relying on the aforementioned protocol to compute encryption keys [10]. However, this approach also faces the issues of latency and additional data transmission.
In our work, we present a solution based on the Advanced Encryption Standard in counter mode which has been modified to fit our auto-synchronization requirement. Setting up the proposed synchronization scheme does not induce any latency, and requires no additional bandwidth in the RTP session (no additional information is sent). Moreover, its parallel structure allows to start decryption on any given frame of the video while leaving a lot of room for further optimization purposes.
References
[1]: N.E.-D.M. Khalifa and H.N. ELmahdy, “The impact of frame rate on securing real time transmission of video over IP networks”, International Conference on Networking and Media Convergence, pp. 57-63, March 2009.
[2]: “Advanced Encryption Standard”, National Institute of Standards and Technology, FIPS-197, November 2001.
[3]: Z. Shahid, M. Chaumont, and W. Puech, “Fast protection of H.264/AVC by selective encryption of CAVLC and CABAC for I and P frames”, IEEE Transactions on CSVT, vol. 21, no. 5, pp. 565-576, May 2011.
[4]: L. Dubois, W. Puech, and J. Blanc-Talon, “Smart selective encryption of CAVLC for H.264/AVC video”, IEEE International Workshop on Information Forensics and Security (WIFS), pp. 1-6, Nov 2011.
[5]: Z. Shahid and W. Puech, “Visual protection of HEVC video by Selective Encryption of CABAC binstrings”, IEEE Transactions on Multimedia, vol. 16, no. 1, pp. 24-36, Jan 2014.
[6]: G. Van Wallendael, A. Boho, J. De Cock, A. Munteanu, and R. Van de Walle, “Encryption for high efficiency video coding with video adaptation capabilities”, IEEE Transactions on Consumer Electronics, vol. 59, no. 3, pp. 634-642, August 2013
[7]: G. Van Wallendael, A. Boho, J. De Cock, A. Munteanu, and R. Van de Walle, “Format-compliant encryption techniques for high efficiency video coding”, in 20th IEEE ICIP, Melbourne, VIC, Sept. 2013.
[8]: M.S. Azzaz, C. Tanougast, S. Sadoudi, A. Dandache, and F. Monteiro, “Real-time image encryption based chaotic synchronized embedded cryptosystems”, 8th IEEE International NEWCAS Conference, pp. 61-64, June 2010.
[9]: Y. Jung and E. Festijo, “Securing RTP packets using per-packet selective encryption scheme for real-time multimedia applications”, 12th IEEE International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), pp. 659-666, July 2013.
[10]: Nan Li, “Research on diffie-hellman key exchange protocol”, 2nd International Conference on Computer Engineering and Technology (ICCET), vol. 4, pp. 634-637, April 2010.